There are many different financial applications available for Android devices across the world. These mobile applications, or apps, provide people with online banking, money transfer, shopping and other financial services. Financial apps usually have multiple security measures in place to protect sensitive data. These measures sometimes include “self-defence mechanisms.” These mechanisms check for a compromised device or application platform tampering. They stop the app from loading and provide a warning message if something seems suspicious. However, little is known about how these mechanisms work. Android financial apps often obscure their code, making observation difficult.
Kim et al. wanted to know more about self-defence mechanisms and the apps that use them. More specifically, they looked at how these mechanisms determine if an application platform or device is compromised and how to precisely identify these mechanisms.
They found two main steps of self-defence mechanisms: checking for “device rooting” and displaying an alert dialogue. Device rooting is gaining access to the highest level of administrative privileges on the device. The researchers developed a tool that generates a human-readable call graph of the methods related to selfdefence mechanisms. This tool locates the self-defence mechanisms in the code of apps.
The researchers then selected 200 random apps from the Finance category of the South Korean Google Play app store. To see which apps used self-defence mechanisms, the researchers tested each app in two conditions: on a “rooted” device; and after altering the app’s binary code. If an app failed to launch or execute properly, the researchers concluded that the app used a self-defence mechanism. They then classified apps on whether they checked for device rooting or app integrity.
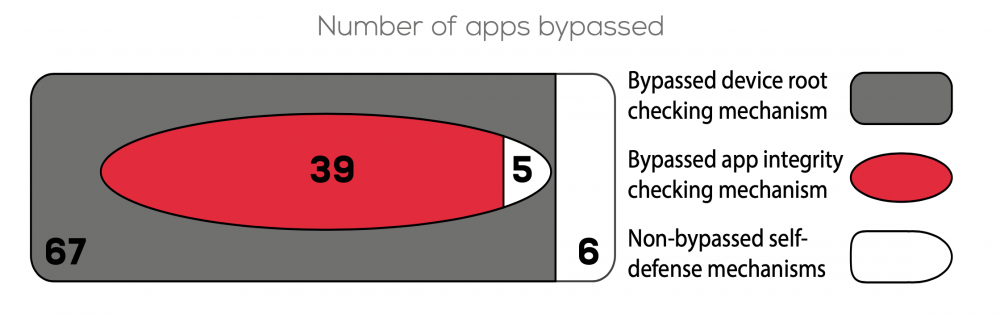
The research team found 76 apps in total that used self-defence mechanisms: 73 of which performed device rooting checks and 44 that checked for app integrity. The researchers then ran their tool on the 76 apps and found that they could successfully bypass the self-defence mechanisms of 67 out of 73 apps utilizing device rooting checks and 39 out of 44 of the apps checking for app integrity. The researchers have indicated that it is possible to bypass nearly 90% of the observed self-defence mechanisms.
The researchers found a way to identify and consequently bypass the self-defence mechanisms in nearly 90% of the apps they studied. This suggests that current self-defence mechanisms are ineffective on their own. There is a need for additional security mechanisms to ensure application and platform integrity for Android financial apps with self-defence mechanisms.
Current mobile financial application defences against malicious code insertion appear to be inadequate.