A traditional approach to online account security focuses on user password choices. Adding strength and complexity to the character combination used in passwords is only one way of enhancing security. Users devote an effort to password selection relative to the perceived consequences of compromise. This effort ranges from negligible, as in the case of trivial accounts, through high-consequence accounts requiring hard-to-guess passwords, to ultra-sensitive accounts requiring multiple forms of authentication. Users will budget their effort to match their view of the risk, so will be reluctant to invest time and energy in complex passwords for low-priority accounts.
This article examines what is known to work, or not work, and what is unknown in password policies. One of the tools available for this research are lists leaked from hacked websites. These databases instructively show which passwords are often used, as well as how often. In light of that evidence, Florencio et al. propose that some notions of password strength and complexity are unhelpful. A combination of characters that is objectively strong (e.g. P@ssword$) when evaluated by an algorithm, might still be vulnerable to guessing. Traditional measures of resilience to password guessing attacks assume passwords are selected randomly. However, evidence shows that people tend to reduce the effort required by re-using common passwords. Password complexity rules that overlook these patterns of use are ineffective at improving password resilience. As a result, complex but commonly used passwords could still be easily guessed. Adding character types marginally improves resistance, but not enough that 'stronger' passwords alone are an effective strategy for web security. There are several types of attack to consider when evaluating password resistance (see table below). An online attack occurs at the public-facing website, when an attacker guesses the correct username and password combination and the server grants access. These attacks can be automated but may be carried out simply with only a browser and web access. An offline attack occurs when an attacker gains access to a stored password file without being detected, and when passwords in the file are one-way encrypted. Some methods to improve resistance to attack are listed in the table below.
Although character combination and special characters provide only minimal security, there are more productive options for channeling user choice of password (e.g. password 'blacklists' that prohibit commonly used choices built from leaked lists). By preventing use of these passwords, administrators can premptively deal with the highest risk selections. However, blacklists might annoy some users and are not a permanent fix, as some common passwords change with time.
Other methods also rest within the control of the site administrator. Key steps in protecting password files from breach include using non-plaintext storage and one-way encryption. To promptly detect leaks, the password file can be spiked with false passwords that signal an attack and the system can lock out users for too many unsuccessful attempts at log in.
The evidence supports increasing site administrators' responsibility for password security. Overall, a single approach to all users or all types of accounts may not be the most effective strategy to ensure security. More rigid limits might be readily accepted by users with high-consequence accounts, while the same restrictions might be prohibitive for those with less investment in a particular online account.
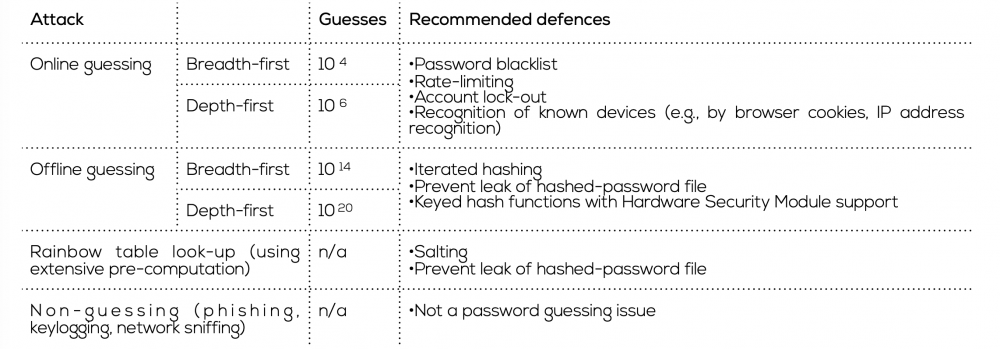
Complex passwords are a small part of password security, reasonable passwords with attentive administration can provide greater protection than user responsibility oriented policy.