Botnets are a major security threat for information systems. A botnet - from ‘robot’ and ‘network’ - is a group of computers that communicate with one another, often for malicious tasks and without the knowledge of the owners of the machines. Interrupting and cleaning up botnet operations has been proven unsuccessful in mitigating their expansion. Various large-scale national anti-botnet initiatives have emerged during the recent years in different countries including Germany, Australia and Japan. The mitigation strategy of these costly national campaigns includes collecting data about infected machines, notifying Internet service providers (ISPs) of botnets in their networks and providing technical support as well as information to end-users.
This study evaluates the impact of national anti-botnet initiatives against Conficker, one of the most widespread botnets of all time. First detected in 2008, Conficker spread through a security vulnerability in Microsoft Windows. Asghari et al. used Conficker traffic data collected from 62 different countries over 6-year period to understand what factors affect the rate of cleanup for infected machines and whether countries with anti-botnet initiatives have better cleanup rates.
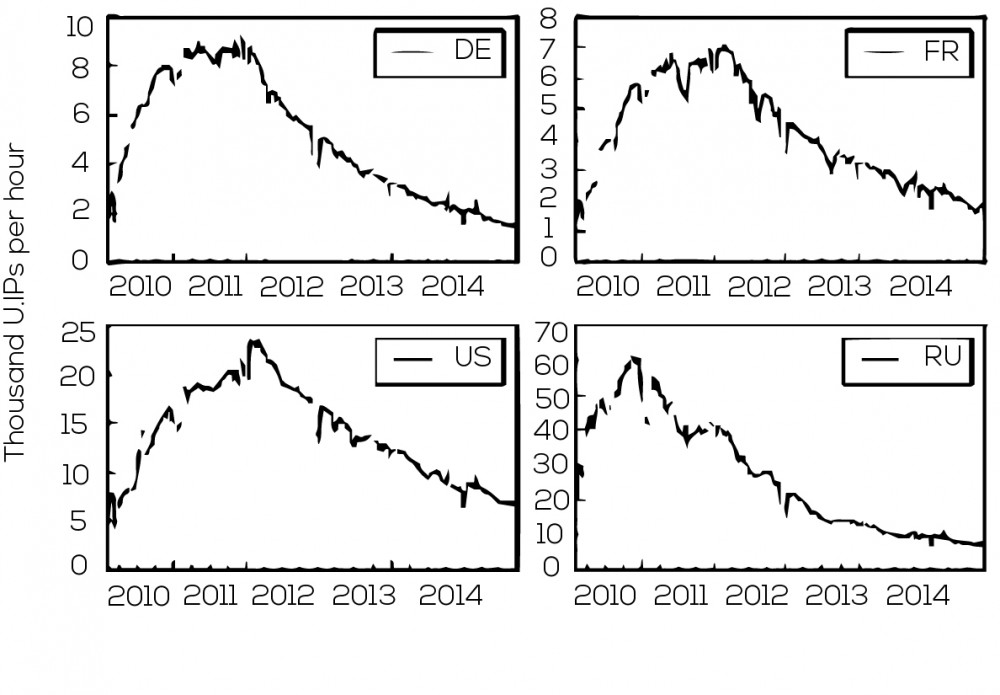
Dynamic Internet Protocol (IP) addresses change frequently, providing a single Internet connected computer with many different addresses over time. This makes a simple count of infected IP addresses an inaccurate estimate of the number of bots. To overcome this issue, an averaged number of unique infected IPs per hour has been used instead. The number has also been normalized to account for the number of Internet subscribers in each country. After these corrections, a similar pattern for all countries emerged from the data. For example, the graphs below show Conficker trends for Germany, United States, France and Russia. In each country, botnet activity shows rapid growth followed by a period of stability before a gradual decline.
This data reveals the variance between the maximum number of bots in each country, relative to the number of Internet subscribers. Surprisingly, there was no meaningful variance between the cleanup rates in countries with national anti-botnet initiatives and those without. These findings raise doubt about the effectiveness of national anti-botnet initiatives. The study also provides a comparison of the Conficker botnet with GameoverZeus, a more recent botnet; this revealed that 15% of computers infected with GameoverZeus are also infected with Conficker. This raises the problem of further victimization of and ongoing harm to vulnerable computers. Interestingly, the number of infections per vulnerable user appeared to be related to the rate of unlicensed software use and to an index for ICT development, which incorporates factors such as a country’s ICT readiness, infrastructure, and skills. These two factors explain the majority of the variation between peak infection rates in different countries.
Short-term national botnet eradication initiatives are not effective. Long term planning for ICT skill increases and unlicensed software reduction is required.