Breaches of businesses computer networks security constitute a great threat to the economic UK’s security. While a lot of attention is payed to the hacking of networks, threats from inside the organisation have also proven to be harmful.
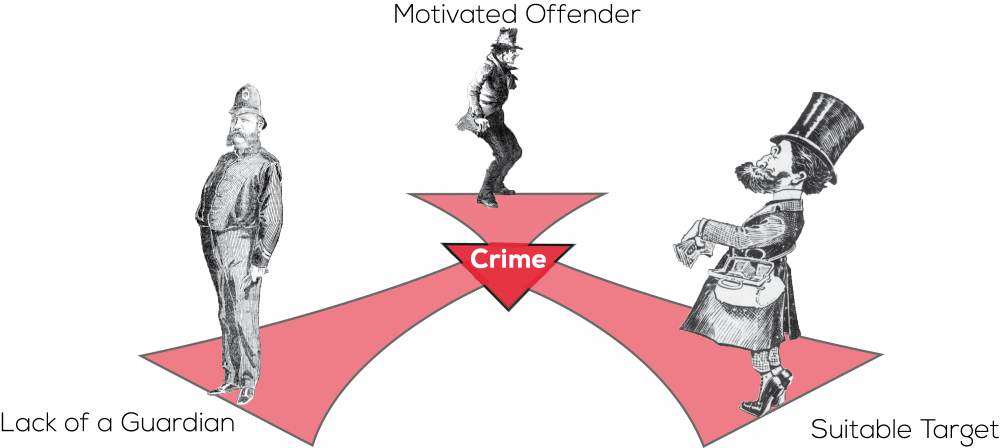
Williams, Levi, Burnap and Gundur tested the applicability of the criminological routine activities theory to insider cybercrime. Routine activities theory proposes that the possibility of a crime increases when a suitable target and a motivated offender meet at a time and place without a capable guardian being present.
To test the theory's applicability to insider cybercrime in organisations, Williams et al. represented its key components as such:
The team used data from the Cardiff University UK Business Cybercrime Victimization Survey to measure the impact of routine activities and guardianship practices on insider cybercrime. All of the private sector organisations in the United Kingdom were grouped into industry sectors and number of employees. Organisations that had no employees other than the owner were removed from the organisations list and offices other than the head office were also removed in cases where companies had more than one office. A list of companies to survey was randomly generated from the list and 751 companies answered questions about their experience with insider cybercrime.
Almost 10 percent of the respondents reported having experienced insider cybercrime. The organisation size was the greatest predictor of insider cybercrime victimization. 37% of organisations with more than 250 employees had experienced insider cybercrime in contrast to 3% of organisations with less than 10 employees.
Guardianship measures and routine activities each explained up to 13% of the difference in the possibility of an organisation becoming a victim of insider cybercrime. The presence of a dedicated cybersecurity manager, worrying over cybercrime and low security awareness were linked to insider cybercrime victimization. The authors suggested that these guardianship measures could have been implemented after organisations had experienced insider cybercrime. The experience of crime leads to worry, which in turn leads to hiring a security manager. Of the routine activities tested in the study, the storing of confidential data, the use of mobile devices and the ability to remotely access organisations’ networks were found to be predictive of the likelihood of victimization.
Interestingly, the use of employee’s own devices (BYOD) and correlation between victimization likelihood and the use of new technologies such as Wi-Fi, social media or cloud services were not a good predictor of insider crime. The researchers suggest that these services to not provide a great opportunity for insider crime as they often include security measures.
While insider cybercrime is still a new research area, this study shows that theories from more developed fields such as criminology may provide a theoretical framework to provide insight into this phenomenon.
Hiring a Security manager and raising awareness about cybersecurity issues may help more than limiting BYOD and Social Media use in reducing the threat of cybercrime by insiders.