The security and vulnerability of modern cars is a significant concern. Computer networks in automobiles can be exploited allowing attackers to control the brakes, steering and engine. Reducing the vulnerability of car computer systems will require a multifaceted approach. Malicious activity inevitably creates unusual behaviour in the internal communication system of cars. The detection of this unusual behaviour in car computer systems provides a last line of defence, and is important for ensuring security throughout the vehicle.
Taylor, Leblanc and Japkowicz sought to develop a framework for detecting abnormal behaviour on vehicle networks. They classified three steps for hacking a car: accessing the vehicle’s electronics, connecting to the vehicle’s network via those electronics and finally sending control messages on that network. This research focused on the last step. Particularly, to detect malicious messages that directly control physical systems. The researchers tested the capability of machine learning to detect attacks against cars. They assessed its effectiveness relative to other forms of detection.
The research team collected 24 hours of internal car network communications from a common, 2012 model family car. They used a type of machine learning that is adaptable enough to be used with car network data known as Recurrent Neural Networks (RNN). Other uses for RNNs include mapping language to predict the next word in a sentence. Seventeen hours of car data was used to train an RNN so it could recognize normal traffic and make predictions about the next messages on the network. A different message from this prediction could be considered abnormal.
They generated indicators of known attack types and inserted them into the remaining seven hours of data. The trained RNN was then tasked with detecting these abnormal patterns in the network data. They compared the performance of the RNN against other forms of detection including probability-based calculations and a simple guessing method.
The researchers found that RNNs were vastly superior to the other methods, which performed no better than a coin flip. Out of four models used, the RNN model working over longer periods of time had the overall best average performance. The authors found that the longer an effect occurs and the more unusual it is, the more detectable it becomes. The exact meaning of the data on a vehicle network is proprietary and as such remained a mystery to researchers outside of the manufacturer. However, the specific ID and field used by the detector appeared to be very important for its performance.
The design and implementation of future systems may be guided by this research in order to increase the safety of drivers and protect them from malicious attacks.
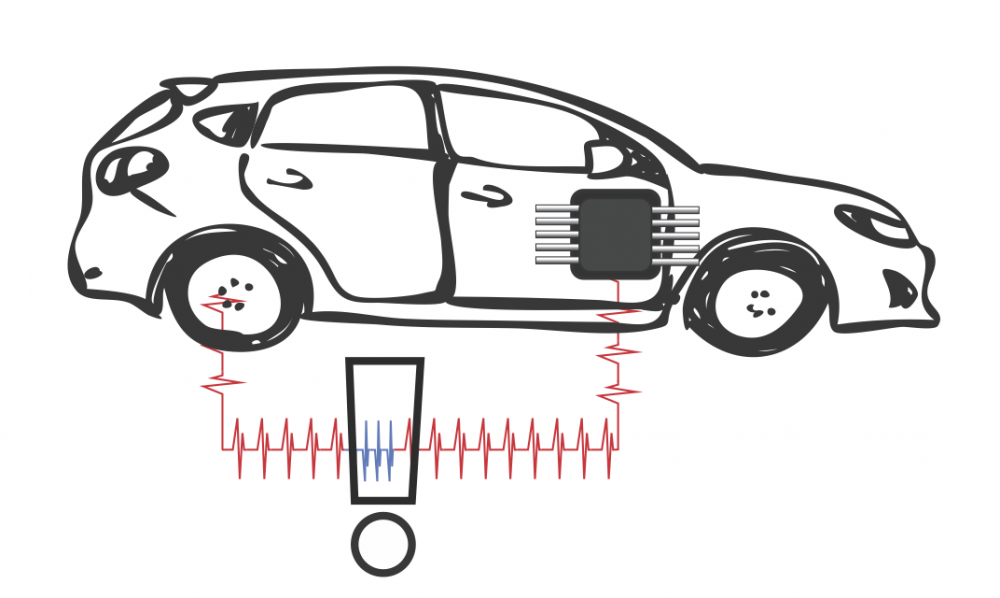
Machine learning appears to be an effective tool for detecting cyberattacks on vehicle communication networks.