Recent increases in security breaches of private data have led to a growing concern about how companies store private information. Large organizations, including banks, communications and social media companies, collect information to aid in their provision of services. Recent cases of malicious leaks have called into question the safety of storing large quantities of data in one place, which is the status quo for these companies. Recently consumers have called for greater ownership and transparency over the uses of their data, while still receiving the same high quality service as before. Bitcoin could provide an answer. The digital currency provides a system of decentralized and transparent online transactions. At the heart of BitCoin lies the blockchain technology. This provides a ledger of transactions in the form of a distributed and tamper resistant database that records all transactions.
Zyskind et al. applied blockchain technology, combined with off-blockchain storage, to create a more secure and transparent mechanism for storing private information. The authors suggest that a decentralized system built on the foundations of blockchain would answer all these concerns. The proposed system has three main components: the users, services and nodes; which are processing locations such as computers. All these actors interact in the blockchain.
There are two types of transactions accepted by blockchain: changes to who can access the data and data storage/retrieval. Both the user and the service provider have access to this data. However, the user retains ownership and can revoke the service provider’s access if the user senses a security breach. The entire system is based on a series of approved transactions. Each one can be thought of as a building block. Because every single transaction is recorded as part of a chain of blocks known as the ‘blockchain’ and is validated by a random selection of nodes, it is nearly impossible to tamper with.
Consider this system at work when a person downloads an app that requires access to their email, location and contact list. When the user signs up for the first time, a new identity shared between user and service provider would be generated and sent to the blockchain with the associated data and permissions. This transaction is then verified by a set of random computers with the blockchain maintaining a record documenting this transaction. The blocks in the blockchain retain a record and timestamp every transaction, which enables both parties to track the use. The data is then stored separately. Now, both the user and the service provider can access the data by sending a retrieval transaction to the blockchain, which verifies the permissions and identity of the access-er. Users are able to view their data transaction and change access control through an online dashboard similar to the centralized wallets used for Bitcoin.
The blockchain allows the user to retain data ownership and provides a resilient data storage solution. Because the stored data can be distributed, a hacker cannot gain access it all in a single breach. Even if someone were to gain access to the blockchain, there is very little harm that could occur. Only “pointers” recording transactions are stored and the data locations are encrypted. In the case that a hacker gains access to both the user’s digital signature and encryption key, only a single set of data is affected since all user-service pairs have their own unique identity.
If implemented widely, this technology could allow companies to increase security without compromising their services data needs. Companies who implement this system would be able to focus on maximizing data utility without having to dedicate large amounts of resources to network resiliency, as the blockchain protects itself. While this technological application is still in the development phases, it appears that blockchain and decentralized trust systems are becoming an increasingly prominent mechanism in the realm of cybersecurity.
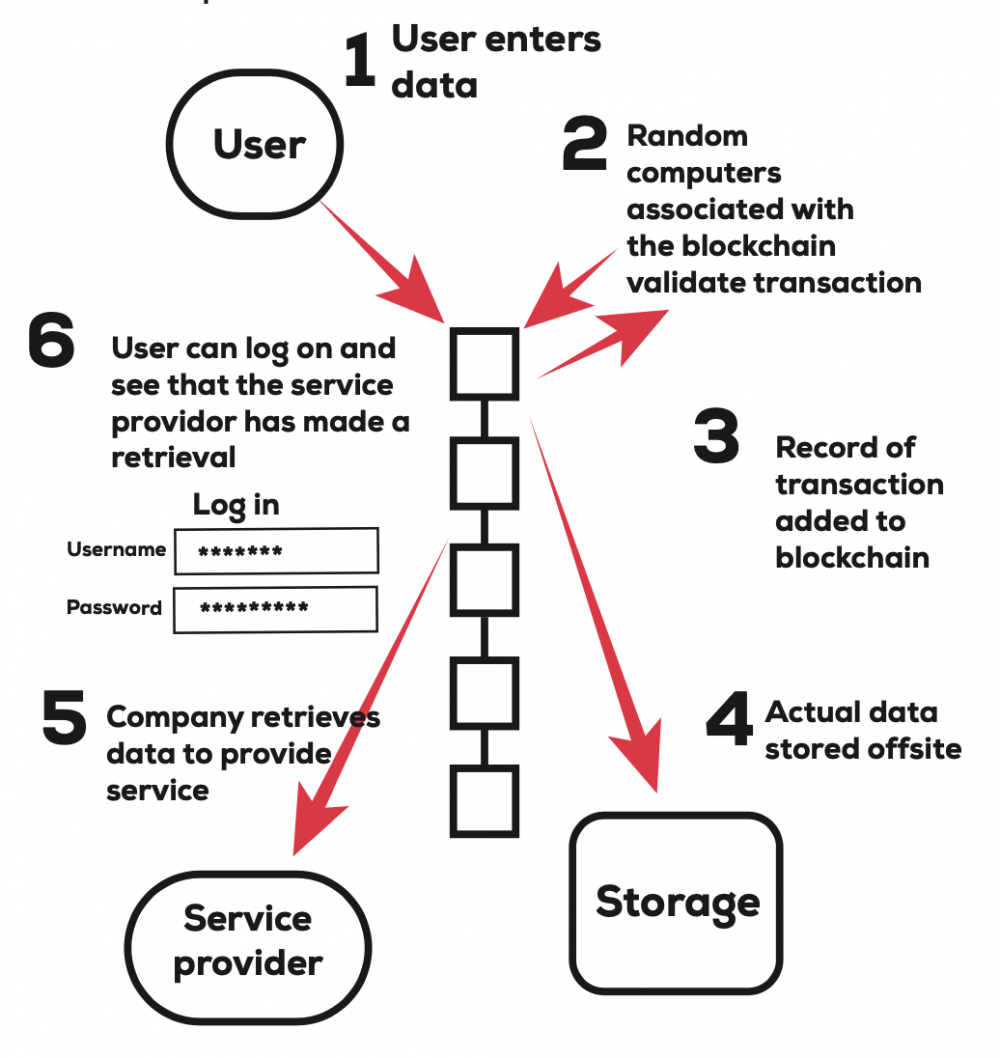
Using a blockchain for personal information allows the user to retain ownership over their data and provides a resilient data storage solution.