The Castle Model is a cybersecurity metaphor that draws from the idea of a traditional castle. High ‘walls’ create an ‘inside’ that is safe from threats ‘outside.’ However, this mindset impedes cybersecurity progress, as it keeps governments and organizations from cooperative opportunities. New technology, such as the automation of attack scenarios and use scenarios such as people bringing their own devices, are incompatible with the Castle Model. Spending a lot of money on this model does not necessarily come with a higher degree of protection.
Leuprecht, Skillicorn and Tait argue that the Castle Model is outmoded. The authors feel that there is a need for a more balanced understanding of cybersecurity. Using key concepts from the Castle Model, they introduce three main arguments to explain their position: organizations are tearing down walls from the inside; technological developments are destroying walls from the outside; and changes in human interaction are blurring the distinction between inside and outside.
Organizations deliberately tear down their own walls and expose themselves to vulnerabilities. There are also high financial and temporal costs associated with the creation and upkeep of walls. Having weaker boundaries in a connected world creates more opportunities to do things faster and better. Second, technological developments are getting better at destroying walls from the outside. As cyberwalls are often bought off-the-shelf, they may contain vulnerabilities that can be broken into by adept attackers. It is becoming increasingly difficult to provide strong boundaries when it is easier than ever to detect and attack vulnerabilities in pre-existing walls. The model also fails to address the possibility of attacks coming from within the walls. It is also difficult to know when exactly a cyberwall is needed. Third, more recent generations, such as millennials interact with technology in a way that dissolves the line between a safe ‘inside’ and a dangerous ‘outside’. They might not have such a strong physical sense of “being at work”. This might lead them to work on confidential subjects in publics locations, unaware of security risks. They are also more likely to provide their own devices to work on, fusing the concepts of an inside and outside based model.
The solution may be not to “fix” the current situation, but instead to respond to these forces differently. A paradigm shift towards thinking of “computing in compromised environments” could be key. This switches the focus from creating and securing a designated safe zone to masking and protecting data while it is at rest and in flight. This could be achieved through the dynamic technologies such as virtual machines and networks, or software and behaviour modelling.
Given the current situation, learning how to operate securely in compromised environments seems more promising than continuing to build higher and thicker walls. Future development should continue looking beyond a singular cybersecurity defence model and consider the use of dynamic and various responses. Modern technologies combined with better authentication may encourage a shift away from the Castle Model and towards a more secure way of thinking.
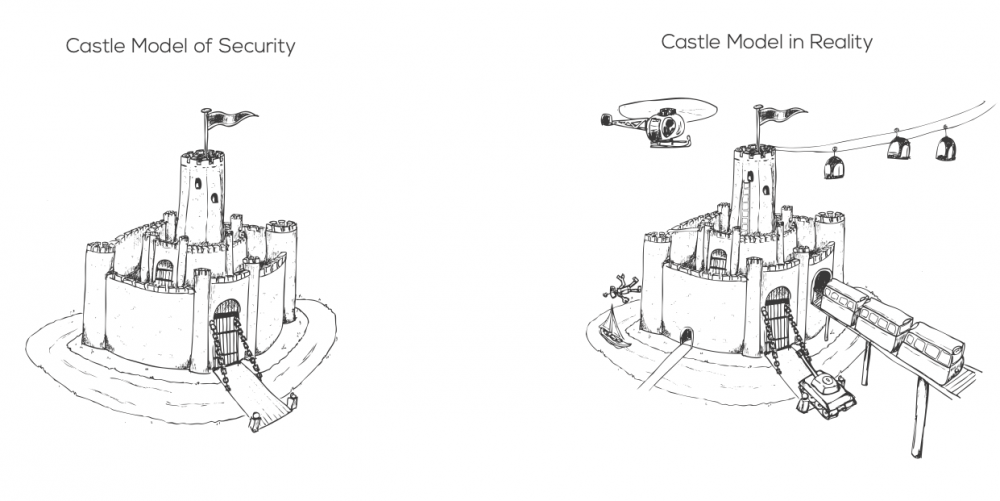
Thinking of security as a series of defendable walls creates an understanding that doesn’t match the real world and leads to inferior decisions.