The Internet has provided new opportunities for all aspects of human activity, including illicit activities. The consumption of Child Sexual Exploitation Material (CSEM) is no exception. Classifications of the consumers of CSEM have generally grouped them into static types. However, little is known about how they might evolve and change over time. Scripts can be used in research to document a reoccurring sequence of events or actions. Analysing crime with scripts provides insight into criminal techniques. It could also help understand of how criminals change as their expertise increases.
Fortin et al. surveyed over 500 academic publications and technical reports that contained key terms pertaining to child pornography and the luring of children (grooming). The behaviours and tools of online sexual offenders were reviewed and grouped into four broad categories of online sexual activities. Making use of the script approach, the researchers grouped the behaviours into episodes and noted the context in which individuals transitioned from one episode to another. Each of the transitions were marked by obstacles that must be overcome in order to progress to the next episode.
There are many types of consumers, each with different motivations, interests and consequently, processes. Scripting these provides an outline of general pathways and the transitions to more serious offences.
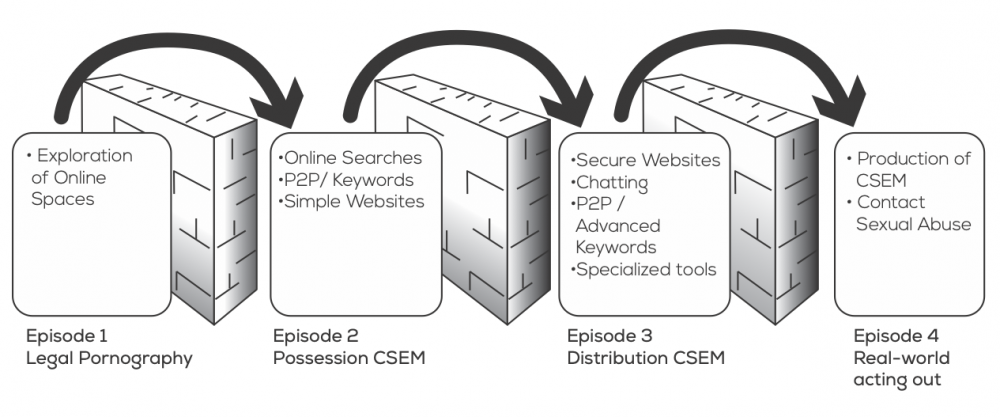
The first episode begins with the consumption of legal pornography. When some people find that it is also possible to access illegal content, their interest shifts.
The second episode sees the exploration of tools that facilitate the discovery of CSEM. When traditional tools no longer suffice for this purpose, the consumer explores virtual spaces and embarks on a process of socialization.
The third episode is distinguished by immersion, as the person interacts more regularly with others in order to access content that is rarer. These interactions help consumers learn how to acquire content and avoid apprehension by law enforcement agencies.
The fourth and final episode involves acting out, with the objects of collections becoming real world targets. Some aggressors use CSEM to facilitate their assaults, others share this content in a bid for peer approval and community status.
This study is not without limitations, but it does provide what appears to be a promising tool for the investigation of CSEM related behaviours.
The analysis of the patterns that precede the sexual assault of children offline could help when designing programs for the prevention of these crimes.