There is global debate about requiring communications service providers to guarantee law enforcement legal access to all data, including encrypted data. This debate highlights the diffculties involved in balancing privacy and security, as the privacy of citizen’s communications on private networks is questioned by governments when those communications are vital to security investigations. This is not a new debate. In the 1990s, the United States government proposed a law requiring that all encrypted data storage and communication systems be designed for “exceptional access” by law enforcement agencies for security purposes. In response to this proposal for exceptional access, a group of computer scientists and security experts conducted a study in 1997 on the potential ramifcations. The authors found that it would have been too diffcult and expensive to implement. Many of the same authors reconvened in 2015 to examine the modern incarnation of the debate in the current operational and technical environment.
An obstacle for the new study was the lack of a complete statement of how governments would conduct exceptional access. Accordingly, the authors used different potential scenarios to illustrate how exceptional access would work. The authors argued that allowing exceptional access would pose greater security risks, hinder innovation, and have commercial and political consequences. Exceptional access would jeopardize current security best practices because it would inevitably lead to more opportunities for hackers to intercept communications. Creating exceptional access would also increase operational complexity. A large number of institutions would have to securely and safely negotiate attacks on the authentication, organisation and information transfer of lawful information access. Increasing the number of stakeholders required would increase the number of targets for criminals. If a third party were trusted with the required information that a law enforcement agency would need to access private communications, then a malicious insider could take advantage of that trust. The authors argued that complexity generally hinders security and increases costs for everyone involved. For example, the United States government would have to increase staffng to accommodate their requirements. Software companies would also be laden with extra costs to engineer their software along the mandated guidelines. Allowing the government exceptional access also limits how communication services providers can construct their software. It also puts communication providers at a competitive disadvantage with frms in other countries.
These arguments go a step beyond just debating if law enforcement agencies should or should not have access to private communications. They deal with the practical realities of exceptional access. Creating exceptional access, although benefcial for law enforcement agencies, could result in additional costs and security risks. The issues highlighted by the researchers are exacerbated by the growing amount of services and connectivity and related cybersecurity issues. Consequently, if governments and law enforcement agencies are going to mandate exceptional access, they should be aware of the possible consequences.
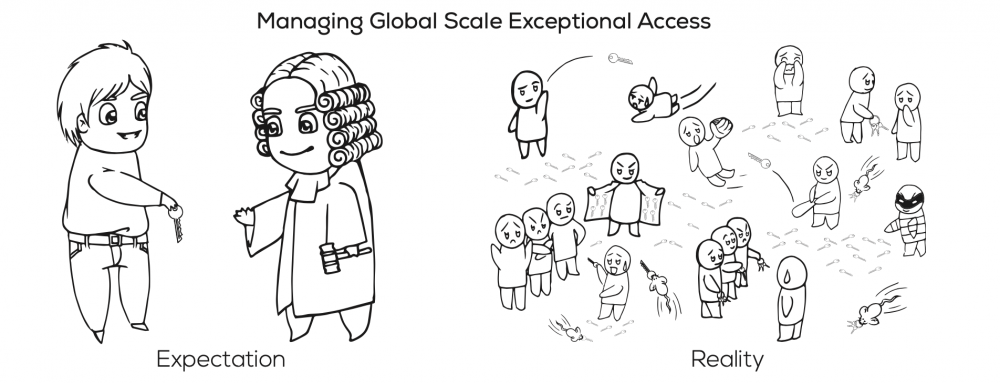
The organizational practicalities of implementing exceptional access to encrypted communications makes them impossible to secure, even if the technology works.